We
tried to cover VXLAN and VXLAN traffic flow earlier.
Every
solution has three main components to it - Management, Control and Data Plane.
NSX
Manager is the management component of VMware NSX solution
We now
try to know more about Data Plane components of NSX.
Data
Plane of NSX has:
·
Logical Switch
·
Logical Router
·
NSX Edge ( NSX Edge has firewall, DHCP relay,
load balancer, NAT and IPSec features
·
Distributed firewall
We will be discussing the NSX distributed firewall in this blog post.
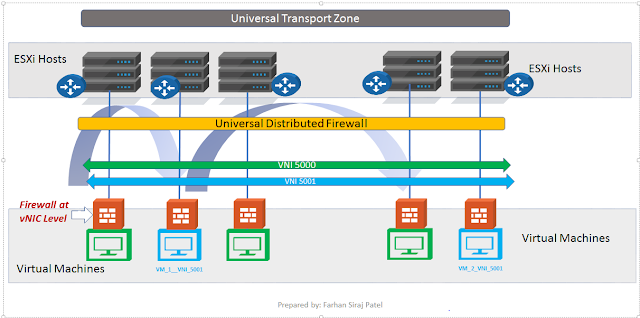
In the
figure above, there is
a.
Transport Zone
Which spans multiple clusters in different sites.
You are able to provision multiple logical switches
within a transport zone.
What is a cluster?
Cluster is collection of hypervisors
b.
Two logical switches with Virtual Network
Identifiers VNIs 5000 and 5001
VNI is used to identify the overlay created over
physical network.
c. We know that virtual machines in NSX infrastructure connect to Logical Switches.
There are two virtual machines connected to
logical switch with VNI 5001
d. Distributed firewall of NSX is applied to each vNIC of all virtual machines.
Features of Distributed
Firewall:
1.
Takes care mainly of East
- West Traffic within your Data Center.
For illustration purpose, figure below illustrates East West traffic within Data Center.
· Data Center Firewall has two logical DMZs
· One for Application Server Farm and the other for Database Server Farm.
Flow of traffic from Application Server towards Database Server is East West in terms of direction.
There is a separate data plane component - NSX Edge Services Gateway which handles north south traffic in a Data Center.
2.
Firewall
is applied at vNIC level of each virtual machine.
Traffic
optimization is achieved here and you don't have unnecessary traffic being
thrown into the external physical network.
If the firewall
policy applied at vNIC level doesn't permit the traffic, the traffic is
blocked closest to the source virtual machine.
Ideally with traditional Data Center networks,
such traffic would traverse northbound towards physical Data Center firewall
and would be dropped by the firewall if the action on firewall is to Deny the
traffic.
3. Distributed firewall rules can be written using
L2 rules or L3/L4 rules.
We need to keep in mind that L2 rules are
enforced before L3/L4 firewall rules.
4.
The throughput of Distributed Firewall improves
as more hypervisors/VTEPs are added to the NSX infra.
Rules in Distributed Firewall can be based on:
i.
Port group
ii.
Logical
switch
iii.
Distributed port group
iv.
Virtual
machine name
v.
Operating
system name
vi.
Data
center
vii.
Cluster
For example you can create a rule on NSX
Distributed Firewall in this way:
Source -
App Logical Switch
Destination -
Database Logical Switch
Destination Port - tcp/1433
This will allow all virtual machines connected to
App Logical Switch to talk to all virtual machines connected to Database
Logical switch over tcp port 1433
5.
Throughput of Distributed Firewall increases as
more and more hypervisors are included.
6.
There is also integration with other vendor
firewalls like Palo Alto.
In addition to
content filtering techniques of Palo Alto firewall,
you are able to integrate other security features of Palo Alto Next Generation
Firewall like vulnerability protection, antivirus, anti-spyware.