Troubleshooting Distributed Firewall in NSX-V
Blog reference:
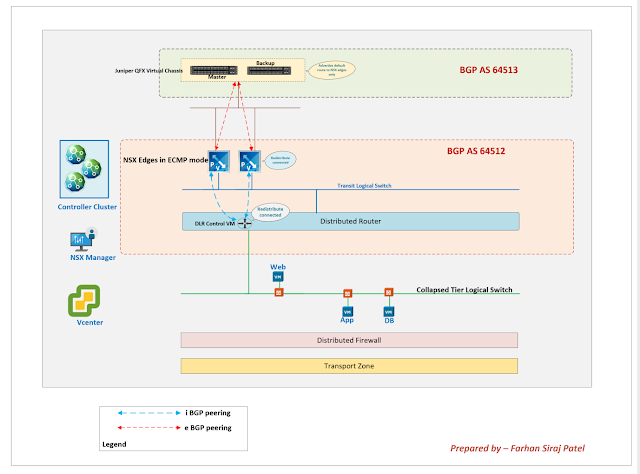
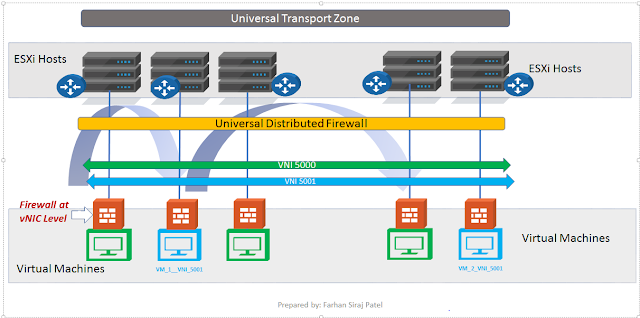
https://docs.vmware.com/en/VMware-NSX-Data-Center-for-vSphere/6.4/com.vmware.nsx.troubleshooting.doc/GUID-20234847-3E7A-4FE8-AEE1-31FFB3652481.htmlIn my earlier post on Microsegmentation, we referenced the below topology and we put the workloads for different tiers - Web, App and DB on the same NSX Logical Switch.
With NSX micro segmentation, firewall is applied at vnic level of each virtual machine.
 |
| Topology |
Below firewall rules are configured on DFW
Notice from the output above that firewall rules are only being applied wherever required using Applied To field
One of the troubleshooting techniques when you are checking DFW issues is to look for the firewall rules being applied at vnic level of a specific VM.
There are two ways of checking the rules
1. From the CLI of host where VM resides.
2. From NSX Manager CLI
1. From the host CLI
We will first get the dvfilter name using below command.
Notice that we are looking for output relevant to the VM name - hr-web
With this, we have got the dvfilter name.
Much easier than checking from NSX Manager CLI as you will notice.
The dvfilter name is nic-70100-eth0-vmware-sfw.2
Now we can check the firewall rules corresponding to this dvfilter using command below.
Look carefully and you will observe that only firewall rules relevant to hr-web-01a have been applied to the vnic of this VM.
From the below pic, only rule number 1, rule number 2 and the default rule is applied to this VM.Rule number 3 is not applied because that is related to app and db virtual machines.
Hence rule number 3 will be applied to the vnic of App and DB virtual machines.
Also notice that logging is enabled for these three rules.

 |
| Filter and check the default deny rule |
 |
| Addr Sets used in DFW rules |
We are keen on checking the address sets and this can be done using the command above.
2. Let's also check the firewall rules applied to vnic of VM from NSX Manager CLI
For this, we will begin by checking the host where our VM resides.
Notice from the output above that the VM resides on host esx-03a
Let's also check the cluster corresponding to this VM
Next up, we need the cluster ID to know the host ID
We now need to find dvfilter for the VM using the host ID, host ID in our case is host-32
Now that we know the dvfilter, we can go ahead and check the rules applied to the vnic of VM
Notice from the output above that you are able to view the TCP rules applied to the vnic of VM hr-web-01a
Corresponding address sets are also listed.
==================================================================
Troubleshooting DFW using Vrealize Log Insight
For the integration of Vrealize Log Insight server along with NSX:
1. We need to forward logs from the hosts to Vrealize Log Insight VRLI server
2. Forward logs of NSX edges and DLR to Vrealize Log Insight Server
3. Forward logs of NSX Manager to VRLI server.
4. Forward logs of NSX controllers to VRLI server.
We will be sending ICMP traffic towards the web server. DFW is blocking this traffic.
We should see this event on the web console of VRLI server.
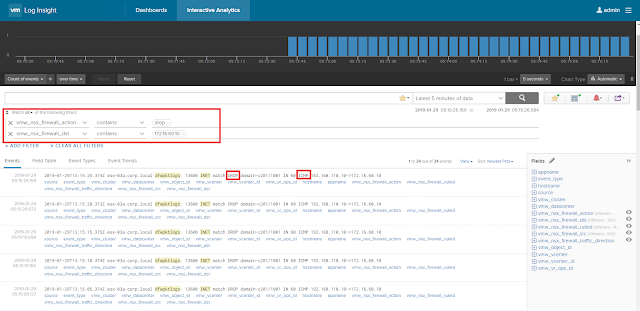 |
| ICMP traffic is blocked by DFW as per configuration |
 |
| HTTPS traffic towards the web server is allowed |